On August 13th, a survey on the security of Ethereum for use in applications was published. Written by academic researchers Huashan Chen, Marcus Pendleton, Laurent Njilla, and Shouhuai Xu, the survey reveals that using blockchain for decentralized applications (DApps) rather than cryptocurrency leaves it open to many kinds of attack.
As Ethereum is now used widely for DApps and underlies many enterprise projects, the authors of the survey saw the need to explain the blockchain’s weaknesses. “Despite the fact that there have been some surveys, they did not offer a systematic and comprehensive view on Ethereum vulnerabilities, attacks, and defenses as we do,” they wrote.
The platform has become a “standard” for application building, now worth over $20 billion with a million executing smart contracts. The complexities involved in these smart contracts and automation on the blockchain bring new security concerns, the survey explains.
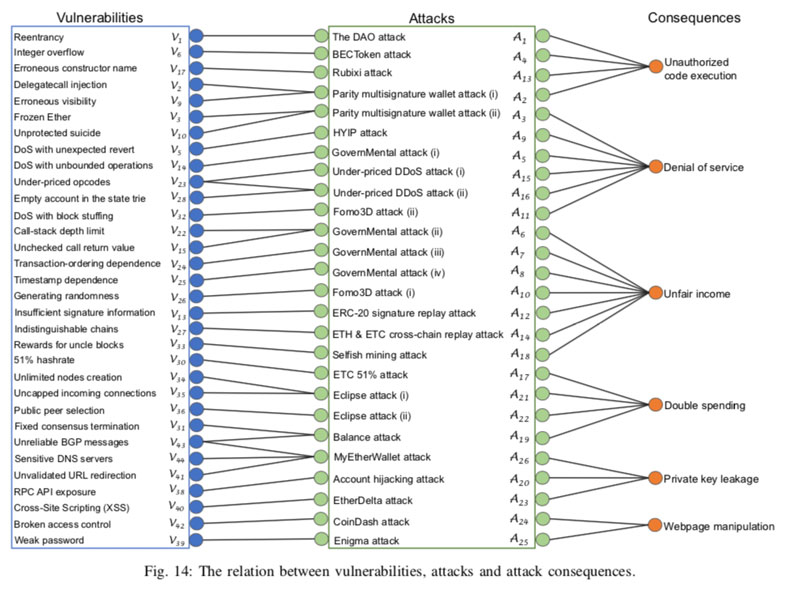
It outlines a total of 44 different types of Ethereum vulnerabilities, 26 of which are in the ‘application layer’ where smart contracts and DApps are built. Indeed, attacks on this layer have incurred over $370 million in losses to date. The report also identifies 47 defenses.
“The vulnerabilities caused by the design and implementation of the Ethereum blockchain are harder to cope with than the other vulnerabilities,” Chen et. Al wrote.
“[This] is interesting because it highlights the difficulty in designing and implementing a secure blockchain platform, despite […] that the vulnerabilities in blockchain may not cause as big losses as the vulnerabilities at the application layer.”
For instance, last year’s popular Ponzi game ‘Fomo3D’ was won by an attacker who made off with around $3 million. The game was designed to be won by the person who bought the last ‘key’ before a timer ran out – while 30 seconds was added to the timer each time a key was bought.
The attacker took advantage of a vulnerability that distracts miners and managed to congest the network so nobody could buy keys. This vulnerability has yet to be eliminated.
The survey doesn’t stop there. Out of the 44 weaknesses, only six have been entirely eliminated. The risk can be reduced by existing best practices. Though these best practices are beneficial, they “alone are not adequate in assuring security.”
So what do the authors recommend developers and businesses do? In short: don’t just chase where money has been lost, defend against all possible attacks. The report suggests a variety of defenses in addition to contract best practices.
“It seems that the defense effort has been driven by the consequential financial loss incurred by the exploitation of certain vulnerabilities,” the survey reads. Considering that nearly 2,500 DApps in various industries are running on the Ethereum blockchain, this is a clear call to arms for more to be done in defending applications.