On Friday the Bybit cryptocurrency exchange suffered a hack in which a transaction for a cold wallet was intercepted, rerouting $1.4 billion in funds to hackers. Today Chainalysis, which is a Bybit partner, confirmed that the hack included a phishing attack. Plus, crypto custody tech firm Galaxy GK8 explored how it worked and how to prevent this sort of attack.
Crypto sleuth ZachXBT quickly named North Korea’s Lazarus Group as the culprit because funds were mixed with those from previous hacks. Chainalysis confirmed this today.
According to Chainalysis, the initial compromise was via social engineering. “The hackers gained access to Bybit’s user interface by executing phishing attacks against the cold wallet signers, leading them to sign malicious transactions that replaced the Safe’s multi-signature wallet implementation contract with a malicious one.”
Update: subsequent forensic analysis showed that the person compromised was a Safe wallet developer, not a Bybit employee, “resulting in the proposal of a disguised malicious transaction“. The smart contract itself was not affected.
Using the developers machine, a piece of malicious javascript was inserted into the Safe user interface code hosted on an Amazon AWS S3 bucket. It specifically targeted the Bybit wallet, so the code change would not be noticed by most users, with the malicious code removed just after the hack. The preliminary forensic reports from Verichains and Sygnia are available here.
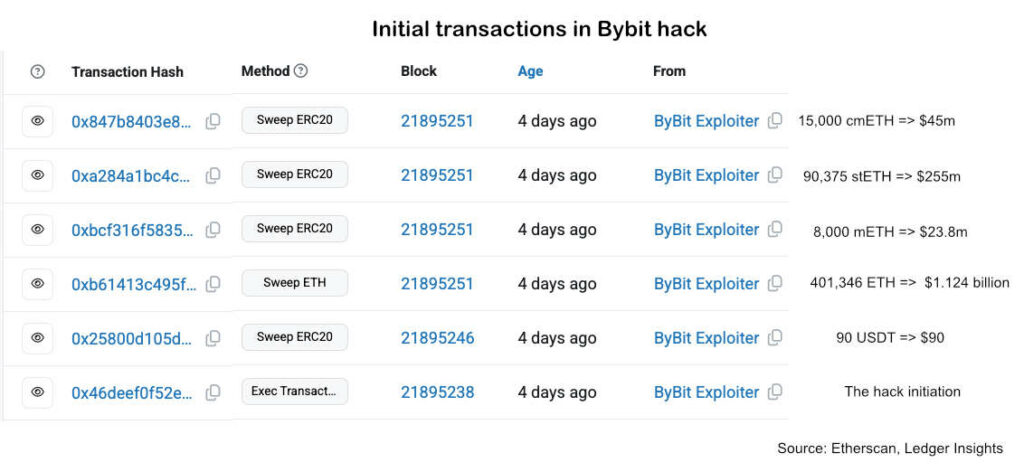
Like Bybit, Chainalysis only mentions a single transaction for 401,000 ETH. However, looking at the transaction history, there were an additional three significant transactions for three different staked ETH tokens totaling $324 million.
Hack analysis by GK8
Turning to custody technology firm, GK8 by Galaxy, their CTO Shahar Shamai took a good look at the transactions and figured out most of what went wrong from the Etherscan blockchain trail. GK8 is not a Bybit partner.
“It’s not like other hacks (where) someone hacked a computer, or social engineering or someone found a vulnerability, an unprotected function in a smart contract. It’s a bit of a mixture of all of these things,” he said. However, he emphasized it was not a vulnerability in the Safe wallet smart contract “but something that is a bit weird”.
Bybit’s cold wallet required multiple signatures to sign a transaction. Based on the initial hack for zero value, Shamai concluded that a hack is possible without compromising all the signers. A hacker only needs to target the person that initially proposes the transaction. They may not be a signatory.
He made this observation before the Safe announcement that confirmed that a disguised malicious transaction was proposed.
When creating the transaction, it’s necessary to specify various parameters, such as the address to send to, the amount and a few other variables. The smart contract for the Safe wallet has an unintuitively named parameter called ‘Operation’. Usually that would be set to zero. However, by using phishing to compromise someone’s computer, the hackers managed to ensure that the parameter was set to ‘1’ with devastating effect.
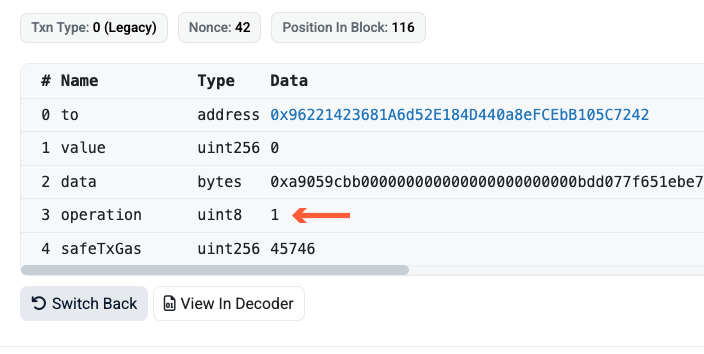
Hence, when reviewing transactions, Mr Shamai observed during the webinar that it was very unlikely that a human being would notice that ‘operation’ was ‘1’ rather than the usual ‘0’.
By setting the operation parameter to ‘1’, it uses a delegateCall function, which effectively transfers the ability to alter parameters to the address it is delegated to. In other words, the hacker now has control over the wallet.
Reviewing the code, we suspect one could protect this by specifying a delegated address.
Complexity creates hacking opportunities
Mr Shamai is not the first to note Bitcoin has a native multi-signature wallet whereas Ethereum lacked one so requires a smart contract. Hence, Bitcoin’s wallet is simpler, and avoids the complexity of a smart contract.
GK8, like many crypto custody technology firms such as Fireblocks and Ripple (Metaco), recommends an MPC wallet instead. This splits the single private key used for signing in to multiple fragments and sidesteps the need for smart contracts.
While Bybit has been praised for its response to the hack event, the phishing issue raises questions about the equipment used to propose and sign transactions. (Update: it turns out it was not Bybit that was phished, but a Safe wallet developer).
There’s a reason why banks have some computers that are not connected to a network and have USB ports disabled. That sort of security is needed for both the transaction proposers and signers (keys).
Air gapped offline cold storage is not a new concept.
As Mr Shamai noted, one could allow outbound network connectivity but block inbound connections. One method is to use a unidirectional cable. Alternatively, he suggested creating a QR code of the transaction to share. We’re not keen on QR codes given it’s not humanly legible.
Of course GK8 has its own solution, the impenetrable vault. It’s an offline device on which the parameters for the transaction are manually set.
One of Mr Shamai’s final takeaways was that if you are going to use smart contracts, then the signers need to know enough about the smart contract parameters to understand them and be able to validate them. That’s the case even if they are not very human readable. However, developers should attempt to make them more user friendly.
We’d add a caveat that these conclusions are not based on Bybit input. If the exchange made mistakes, they learned the lesson the hardest way. But it appears their systems were not compromised. It was the machine of a Safe wallet developer
Update: added that the compromised machine was a Safe wallet developer, not a Bybit employee.






