Today the Nordic BIS Innovation Hub published two papers for Project Polaris on cybersecurity. One paper is about threat assessments using learnings from the DeFi sphere. And the other is a CBDC cybersecurity framework.
Most retail central bank digital currencies (CBDC) will be two-tiered with commercial banks often providing the wallet user interface. However, the reputational risks of something going wrong will often rest with the central bank.
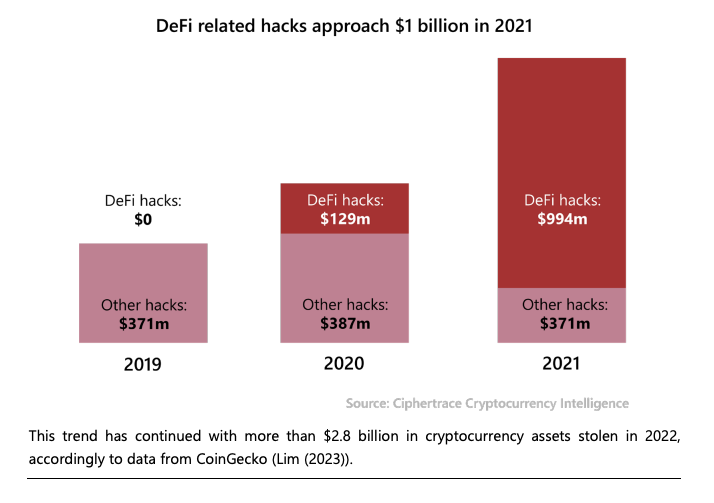
There’s a daunting list of cybersecurity risks, but many of these exist today for other payment systems. However, a few do not. For example, digital currencies add programmable and automated payments. The paper points to DeFi smart contract hacks as evidence of the sort of losses that hacks could cause.
Cyber threats are modeled using the MITRE ATT&CK framework. However, the BIS concluded that there are gaps in existing techniques when it comes to novel technologies such as DLT and smart contracts.
“While DeFi is not a synonym for CBDCs, several of the current operational retail CBDC implementations are based on a similar technology stack or make use of one or more of DLT, smart contracts, tokens, digital identities and immutable data. This allows DeFi to serve as the starting point for this analysis of CBDC,” the authors wrote.
The CBDC cybersecurity framework
The other paper focuses on a CBDC cybersecurity framework.
“It is assumed that a CBDC system would be complex, with a large attack surface and many potential points of failure, bringing new and elevated risks,” the authors wrote.
To an outsider, the risks appear daunting. Here’s a list of the sources that could be gunning for the CBDC:
- Nation states or nation state-sponsored groups
- Organised crime groups
- Hacktivist groups
- Lone hackers or petty criminals
- Professional criminals
- Insiders
- Malicious end users
- Hacked third party tech providers
- Natural or human-caused disasters
- Cyber warfare vendors
- AI bots.
The list of attack events is a bit longer. But Project Polaris provides a seven step framework to address the risks: Prepare, Identify, Protect, Detect, Respond, Recover and Adapt. Each comes with a checklist, some of which have 30 or more points.
The paper concludes, “The framework helps central banks identify areas that need development, both inside the central bank and across the jurisdiction, and could help inform technology providers on the opportunities and expectations awaiting them.”
Meanwhile, the other output from Project Polaris was a book outlining the offline CBDC options.






